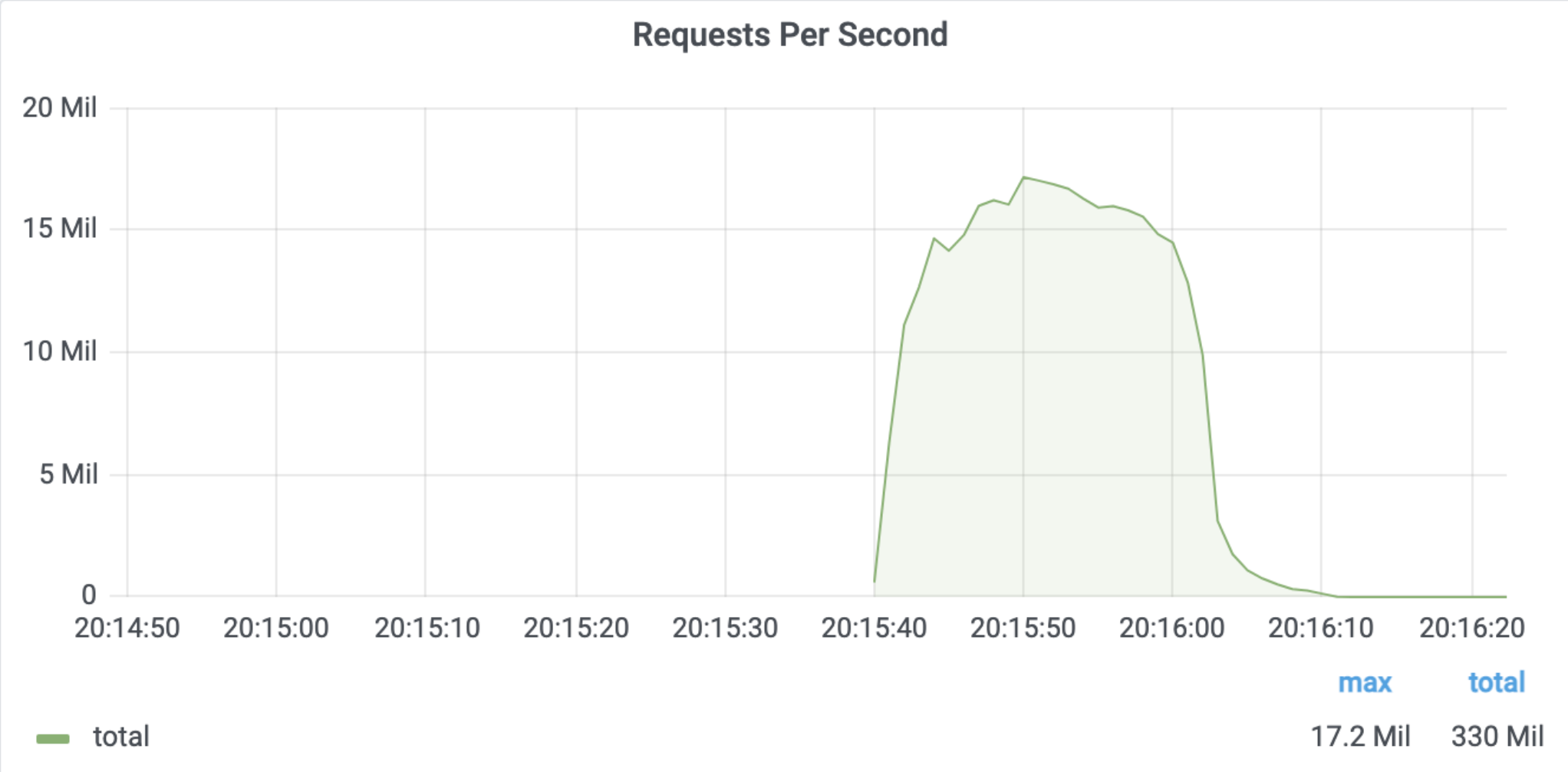
DDoS is a variant of the DoS attack. In this article, you will learn about the types of such attacks and, above all, how to protect yourself against distributed denial of service attacks.
Table of contents:
- What is DDoS and what do you need to know about it?
- What are the most common types of DDoS attacks?
- How to mitigate the effects of a DDoS attack?
- Malicious traffic prevention – things to remember
What is DDoS and what do you need to know about it?
A Denial of Service (DoS) is a type of computer/system/network service attack aimed at temporarily stopping its operation. Among the multitude of DoS attacks, we can find so-called teardrop attacks (or, fragmentation attacks), aimed at accumulating the buggy packets at the victim's machine, leading to its ultimate crash. Luckily, modern networking devices are trained to spot such attack vectors right away, blocking the very first packet the minute a teardrop attack starts.
DDoS adds another layer to the definition, as the attack is now distributed; being carried out from a large number of different source addresses at once, including a group of people, bots, or infected systems/devices. One of the most well-documented network layer attacks happened at the University of Minnesota in the summer of 1999. With the use of the Trin00 tool (in short; a botted network for generating DDoS traffic; aimed mainly at web servers), the attacker managed to shut down the university's computer network for more than two days.
As we can learn from the CERT advisory 99-04, a typical malicious network was then composed of a small number of servers [masters], and a large number of infected clients [daemons]. To initiate an attack, the attacker sent DoS instructions to the Masters, which passed them to the Daemons – starting to flood the destination IP address with UDP packets. All that behind the backs of unaware owners of compromised IPs. If you want more details on the Trin00 attack tool, we recommend reading the linked CETR advisory.
Still, as technology has made a huge leap since 1999, DDoS tools are much more sophisticated and more accessible now. As the methods surely change, the above example illustrates how compromised networks can be exploited for quick leverage. And how web-based attacks could be controlled remotely to exploit vulnerabilities in virtually every machine on the planet.
Who is the main target of a DDoS attack?
Before we answer who, let us quickly ask: why. Amplification attacks are usually carried out to noticeably slow down or temporarily block a service. So – instead of hacking the chosen server and simply stealing the data, removing chunks of code, or changing the passwords – threat actors decide to impose an increased user interest, flooding the server with thousands of requests (at once).
In fact, the number of queries is such a brute force [or is generated in such a way] that the network infrastructure, system, or application serving the service will simply exhaust its resources, denying access to any legitimate user outside the attacking network.
Now, this could be perceived from two different perspectives.
In an ideal world, the attacked organization would notice the abnormal activity right away. In fact, they usually do when the server is already blocked. DDoS attacks focus on sectors of web-based services, including government, healthcare, e-commerce, banks, and gaming. There is no rule for being included or excluded from the potential attack. Some of them will try to damage your reputation (among certain markets) or generate a loss (i.e. by blocking your shop during the sales season). Other attackers will ask for a ransom or simply block your content delivery network "because they can". Consequences for your business may also include increased insurance costs, loss of access to critical data, and, obviously, loss of business opportunities.
Aside from purposely harming your reputation, such methods could also be aimed at spreading panic (or misinformation) among users of your service. Remember that the most common result of a DDoS attack is to prevent legitimate users from accessing or using a certain service.
So, if you represent a trustworthy source of information, an HTTP flood could block your site temporarily and, for example, move all the traffic (with the use of redirection) to a fake version of it. Or force your users to search for some version of your blocked online services. This could lead to thousands of people sharing their credentials with the malicious web pages, making critical decisions based on false information, and even influencing their liking or trust in specific services, brands, or websites (as well as the companies that stand behind them). They could also download malicious software.
To summarize, the goal of DDoS attackers is not to hack and steal information, but to slow down or disable the service. Flood attacks could be conducted for mere fun and to test the endurance of a target system, but they can also be based on financial gain or ideology. Aside from ransom requests (for disabling an attack) and purposeful harm to the company’s finances /reputation; the hacker may also use DDoS as a smokescreen for covering a more advanced hacking method – aimed at something much bigger.
We now know ‘who’. Let’s learn more about the ‘how’.
What are the most common types of DDoS attacks?
1. Protocol attacks
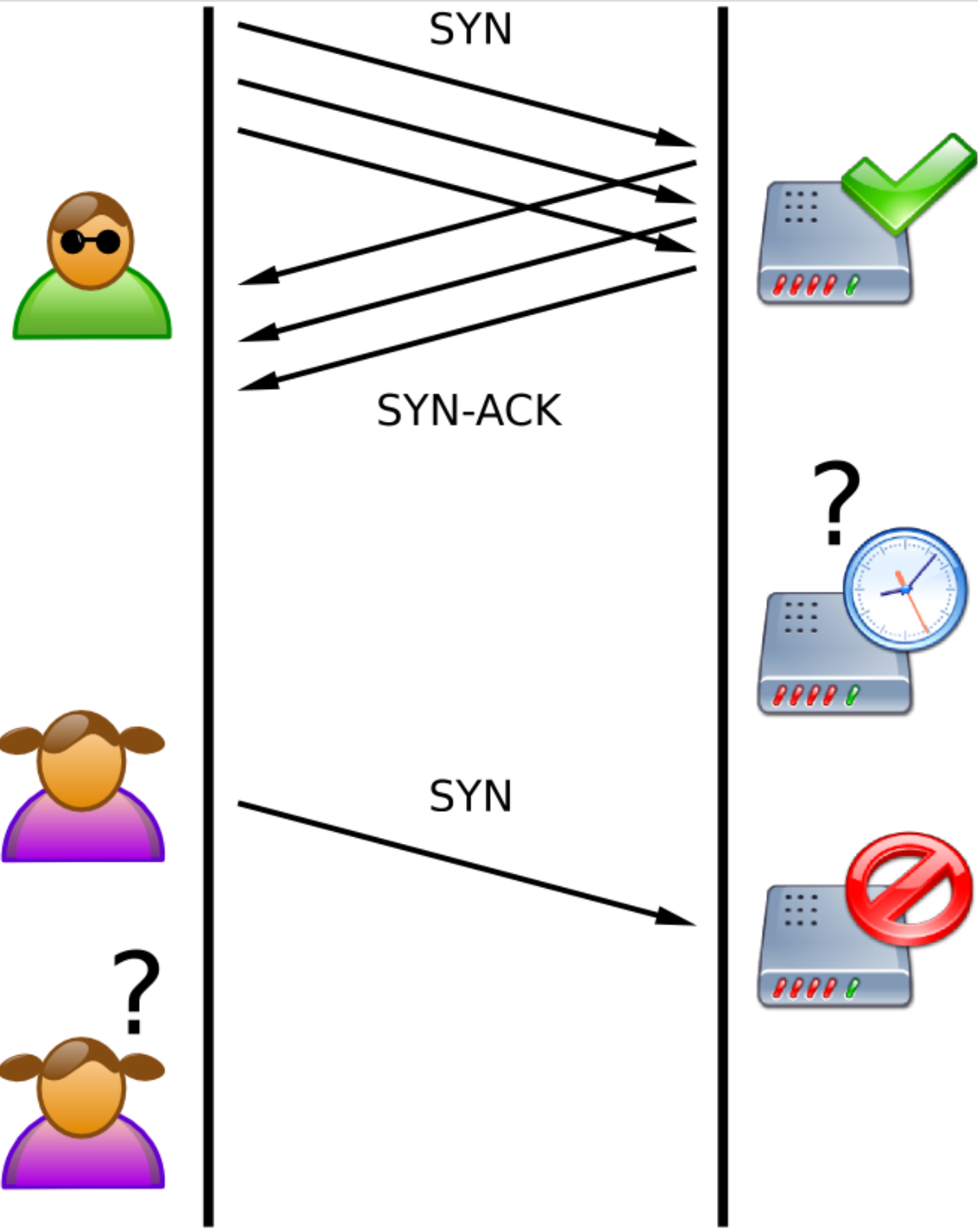
The main goal here is to exhaust all of the resources of a certain target network/service by feeding it a series of bogus initial connection request(s) – so, essentially, to create bogus traffic. One of the most used types of protocol attack is an SYN flood attack. It occurs when a large number of SYN packets are sent to every port of a targeted server using faked IP addresses. Because the client didn't send any SYN packets before, the host responded with an SYN-ACK.
The attack traffic can overload the target’s memory buffers with partial packets, and slow and malformed pings, resulting in the system's crash. The host computer's ports will eventually become overburdened with half-open connections, and valid initial connection requests will be refused. In most cases, a firewall can't deal with DDoS floods on its own, as the target is hit with too many protocol attacks at once.
The efficiency is often measured in packets per second (pps). In addition to SYN floods, there are many other types of similar attacks, like Ping of Death, or Smurf.
2. Volumetric attacks
Volumetric DDOS attacks are the most common and most devastating. They are frequently carried out via User Datagram Protocol (UDP) and Internet Control Message Protocol (ICMP) floods, sending thousands of fake error requests to the target. UDP and ICMP are connectionless protocols that enable rapid data delivery without relying on integrity checks, which makes them excellent targets for attackers.
Volumetric attacks ensure that practically any machine’s network bandwidth is overwhelmed by flooding every available open port on a device by sending massive data requests. To increase those numbers even more, attack tools' performance is usually boosted with reflection and amplification techniques. As a result, the target machine isn't able to respond to legitimate traffic because its attention is focused on evaluating fraudulent requests for data.
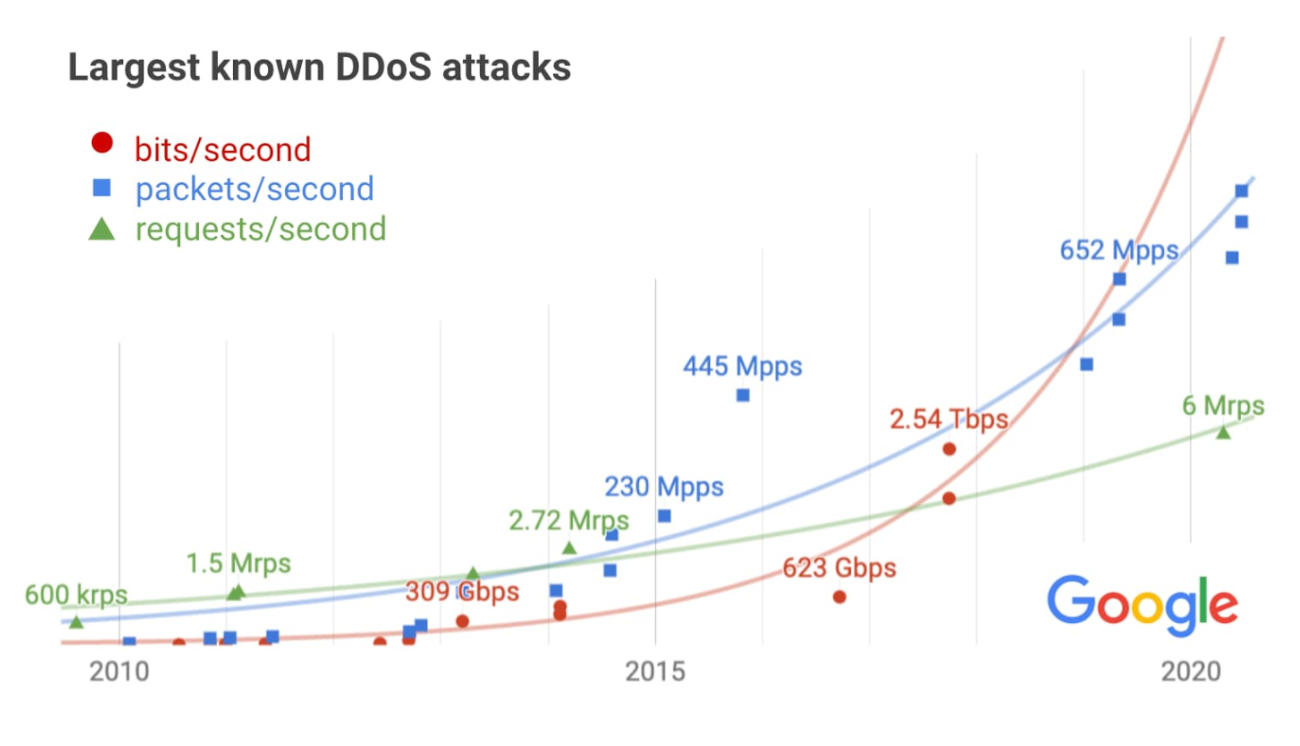
They are often measured in bits per second (bps). And if you want to imagine the scale of how DDoS attacks work, let us tell you that in 2017, Google was the target of the largest DDoS attack, which was measured at 2.54Tbps.
3. Application-layer attacks
Application attacks try to compromise a company's direct web traffic by sending a large number of seemingly valid processing requests to the application, with the target venues being SMTP, HTTP, HTTPS, or DNS server(s). Attackers flood application processes with several concurrent requests, aiming to cause the server to crash. They force the application to exhaust memory resources until it is unable to respond to any legitimate requests.
The application layer is the uppermost layer of the OSI network architecture and the layer that has the most direct interaction with system users. As a result, identifying application-layer DDoS attacks is difficult, as they typically involve only a few machines, if not a single one. As a result, a server may fall victim to the deception of an increased volume of valid traffic. They are measured in requests per second (rps).
What are the most common types of software used to conduct DDoS attacks?
- The Low Orbit Ion Cannon (LOIC) is widely used to flood TCP, UDP, and HTTP traffic, while the High Orbit Ion Cannon (HOIC) allows hacktivists to easily send bulk GET and POST HTTP requests.
- hping3 is a console program similar to the ping utility. However, it offers much more functionality than sending ICMP Echo Requests. Hping3 supports TCP, UDP, ICMP, and RAW IP protocols, port scanning, and IP spoofing.
- R.U.D.Y. (R-U-Dead-Yet) sends an HTTP POST request with an incorrect "content-length" header length, then injects the information, in short, single-byte packets into the form. The data is minimal and transmitted slowly, causing a backlog of application threads and preventing the server from ending the connection. The server's connection table overflows, rendering it unusable.
- Mirai is used for creating DDoS botnets through the IoT. It installs on devices with default passwords, connects to IRC servers, and waits for a signal to attack the chosen server. Malware is very easy to detect by antivirus software and does not attempt to hide from it; company printers, IP cameras, and household appliances are typically not protected in this manner.
How to mitigate the effects of a DDoS Attack?
So how do we know if we are a targeted victim of a DDoS attack? Apart from switching off the service or its obvious slowdown, it is difficult to "notice" a cyber attack right away. After all, under normal conditions, no one is constantly browsing their website, and before we realize that we have become the target of an attack, customers who have problems with the proper operation of the service might already notify us about it.
In the first reflex, we usually check the status of the service (i.e., the targeted website), observing high network traffic and exhausting hardware resources. Now, you should calm down as your next steps should neutralize attacks in such a way that the service is constantly available to users.
First of all, if you’re caught in the middle of an attack, there’s not much to be done without proper preparation. Let’s move on to that.
DDOS mitigation: prevention, preparation, planning
As we explained before, a distributed denial of service attack can target any organization that provides an internet-facing service. That’s why you should prepare a response plan for similar incidents in advance. While discussing your mitigation efforts, try to include the following:
- Verify whether the network capacity is adequate. Have you recently managed to slow down your server (i.e. with internet traffic)? Has your company's bandwidth been raised to accommodate the increasing usage (due to remote work)? We also recommend ensuring capacity and performance standards for networks, systems, and applications.
- Make a list of all internet-facing services and prioritize those that require DDOS protection. Which potentially targeted websites are crucial to your business? Now think about the consequences of blocking them for several hours. How would you communicate the problem to your target users? Partners?
- Identify vulnerable systems. Apply software and firmware updates, as well as security patches, to all network equipment and servers regularly. Unplug or uninstall every broken device from your network so it does not become a part of the botnet, which is used to conduct HTTP floods.
- Use numerous ISPs (Internet Service Providers) to provide redundancy and/or load distribution. For example, some businesses utilize one ISP for public-facing websites and services and another for VPNs and other internal corporate activities. Consult with your Internet service providers (ISPs) in advance to see what protections and help they can offer.
- Avoid exposing superfluous ports or services to the internet, which could make them targets. Most businesses do not need to expose NTP to the public internet. If there isn't a legitimate business need for ICMP, CLDAP, SMB, Chargen, or Ripv1, cut or limit the amount of bandwidth they use.
- Secure coding practices can help reduce risks and make sure that the parts of the application work well.
- Consider hiring a DDoS consultant/service provider who will monitor and respond to attacks on your resources automatically. When you use these kinds of services, make sure you fully understand their service level agreement, which talks about detection levels and how long it will take to fix the problem.
The best way to mitigate DDoS attacks is to plan to decrease the vulnerability of your services to hacking. Employ behavioral traffic analysis by establishing the continuous and automatic analysis of traffic to the service as well as its external monitoring and measurement of response times. Proper configuration of alerts can help to detect an attack with minimal delay.
Malicious traffic prevention – things to remember
A massive DDoS attack is quite simple to carry out. All the hacker needs is a reason to use it. Your small business may not appear to be a top priority for nation-state actors; however, a disgruntled former employee, competitor, or student with limited resources (as little, as, $60 needed to block your service for 24 hours) can launch an attack. And given the ease with which a typical DDOS attack can be conducted, businesses should set up controls and have a plan in case they get hit. For that, we strongly advise using DDOS mitigation services.
While using (multiple) compromised computer systems is not legal, DDoS-for-hire businesses are advertised online as booters or stressors that can be used to test the resilience of a targeted web server. The issue is that they rarely ask whether you have permission to run such stress tests on a chosen target. All you need to do is to create a login and password (sometimes not even that!), enter the target IP, port, and time duration, then hit the Launch button. As a result, practically anyone can hire similar ‘testers’ anonymously to attack any target of their choice.
So, when we speak about managing this risk properly and avoiding multidimensional consequences, we advise you to include a DDoS response plan in advance and consult your strategy with an experienced cybersecurity specialist.
And if you wish to discuss other cybersec-related topics or need a hand reviewing your cybersec strategy, go ahead and contact us.