Social engineering, also known as social hacking, refers to any method of breaching security that relies on human nature rather than technology. It’s used to obtain sensitive information, gain access to physical and digital resources, install malware, and persuade victims to perform risky actions.
Table of contents:
- Social engineering: meaning and definition
- Social engineering attack examples
- Social engineering & cyber security – summary
Cybercrime reached an all-time high during the COVID-19 pandemic's peak. According to the latest Cybersecurity Awareness Month update by NCSA, phishing attacks have accounted for more than 80% of reported security incidents since the outbreak began in 2020. And, as Cisco’s 2021 Cyber Security Tech Trends report points out, a crushing 86% of respondents revealed that at least one of their employees had tried to connect [clicked] on a phishing site in the last year.
Why are those statistics important? Let’s dig into the basics of psychological hacking.
Social engineering: meaning and definition
Manipulation 101: repetition x emotions x repetition
Social engineering is the art and science of skillfully manipulating human behavior. It encompasses all forms of leveraging influence to persuade someone to act in a certain way or make decisions that benefit us (as a manipulator).
Although it may appear unethical, social engineering is widely used in advertising to persuade millions of people to buy specific products, services, or even think in a certain way. Think about today's standards for personal devices (which brand? why?), after-work activities (what inspired you to choose them?), the clothes you want to own, and the concept of fashion in general. Which food items do you prefer to buy (why brand X, not Y?). What music genre is suddenly on top? Or maybe recently, you felt the urge to subscribe to a specific streaming service? Own a specific pet breed?
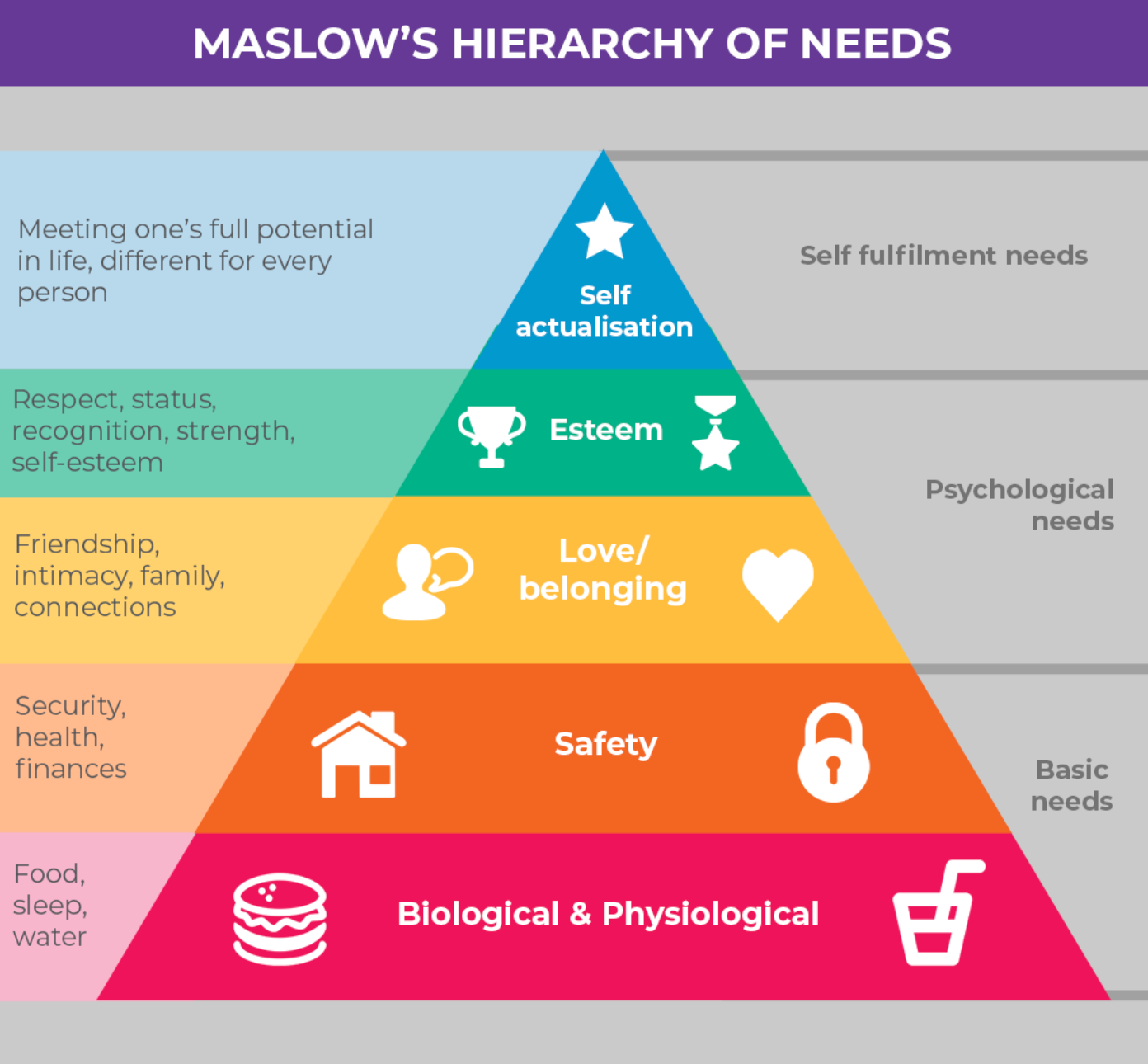
Sadly, no one is fully resistant to advertisements as the constant repetition in multiple media burns them into our subconscious, connecting purchasing advertised products with "achieving" respect, beauty, status, or even happiness and self-fulfillment, which implies a more successful life. Those very needs are listed on the upper half of Maslov’s Hierarchy of Needs – so no, there’s no way we can simply ignore them.
Still, some advertisements might be used to promote noble values, encouraging their audiences to recycle, reduce water waste, avoid drinking and driving, or help people in general. Cybercriminals, on the other hand, are not so charitable.
Why do cybercriminals prefer social engineering?
Let’s start with a fact: the vast majority of cybercrimes involve some form of social engineering. The main goal of a social engineering attack is to trick its victims into unwillingly acting or revealing sensitive information that compromises their company's security.
Why would they do that, you may ask?
Because of the very same Maslov’s Pyramid. Social hacking usually aims at the middle layers of it [hitting much closer to its base = our basic needs], praying on needs for Safety and Love/Belonging. Generally speaking, Safety addresses one’s desire to have a "secure" income (= a stable job), so you can afford your lifestyle while Belonging relies on our desire to (closely) connect with people. We can conclude at this point that, in general, people are willing to do anything to keep their job and maintain their social interactions.
And social engineering addresses precisely those needs, preying in particular on two emotions: fear and trust. That’s why when attempting to breach a business, cybercriminals can rely on one consistent factor: human error, caused by the specifics of our nature. Keep in mind that, because of such a unique factor involved in cyberattacks, anyone at any level of the organization may be already one click away from a potential attack on themselves.
Like with ads, once dragged in the loop of a new product, you’d be surrounded by its promo materials everywhere you go (until the purchase). Similarly, a victim will be taunted and exploited until the purpose of hacking is achieved. This time, however, the victim’s credentials might be re-sold multiple times via the dark web.
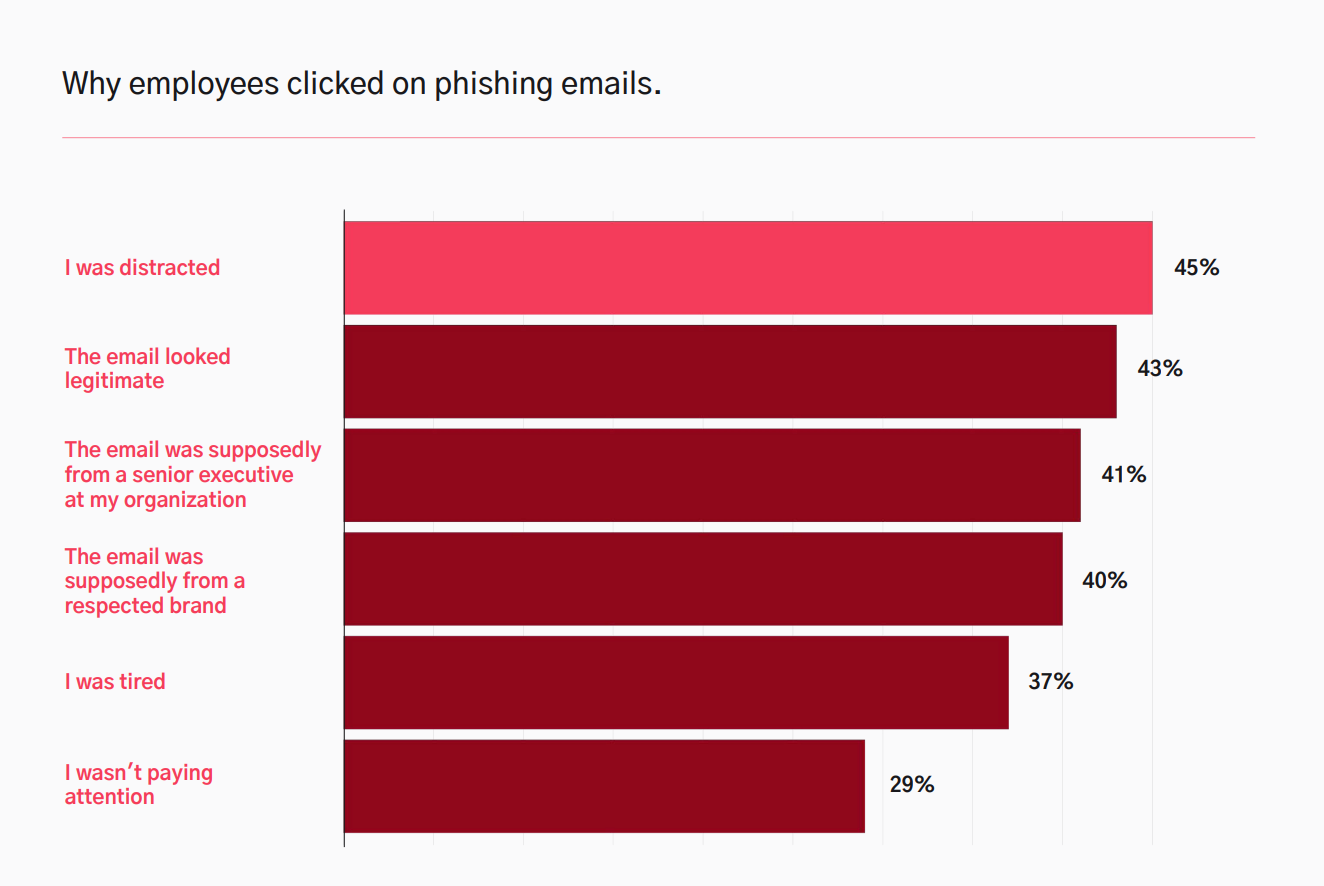
Threat actors use a lot of psychological tricks to get information that they can then use to their advantage. Some hackers will use authority, sharing their malware in a message disguised as an update request from your senior manager/external service provider or instruction sent by local law enforcement. They might persuade a victim to share sensitive information with a bad actor by posing as an executive at the target organization.
The other will use social proof and peer pressure, [falsely] claiming that other colleagues have already complied with given requests (i.e. for updating their passwords in the linked bogus database.) This method is especially dangerous in times of remote working, where employees might not be able to verify whether such a file is made by the company – especially when he sees all his coworkers listed in the file.
Some victims may react to reciprocity by believing that their data safety breach is, in fact, a return for a [usually generous] favor. Others will find themselves trapped by the Commitment/ Liking of this amazing new friend, who gradually seems to be more and more interested in the chosen company.
It’s worth mentioning that a threat actor will not behave like a typical spam account: their fake persona will seem like a genuine one, conversational, with good language skills matching the tone of communication and the industry. They will reach out to you from an email/website/social media account almost identical to the original (already known) one. They will answer your phone. Sometimes meet you in person. And write back if you decide to keep the conversation going.
Social engineering is a popular method among hackers because the process relies simply on gaining the victim's trust. If conducted properly, it’s the quickest route to unnoticeably collect a full set of credentials needed for a data breach. And, as commercials tend to work better while built on emotions, social hackers are especially active in times of chaos and uncertainty. That's a big reason for 2020's massive cybercrime boom; a plethora of targets who were (and still are) unsettled, scared, and stressed created a target-rich environment.
Social engineering attack examples
People are the weakest link in any security system. With proper skills, they are much easier to hack than machines. That is what makes these schemes difficult to detect and resist. Additionally, the scope of manipulative techniques is constantly growing, adapting to emerging technologies, social behavior changes, and the latest news. Threat actors can learn vital sensitive information or manipulate the behavior of others by using scams, confidence tricks, and personal information obtained from other sources.
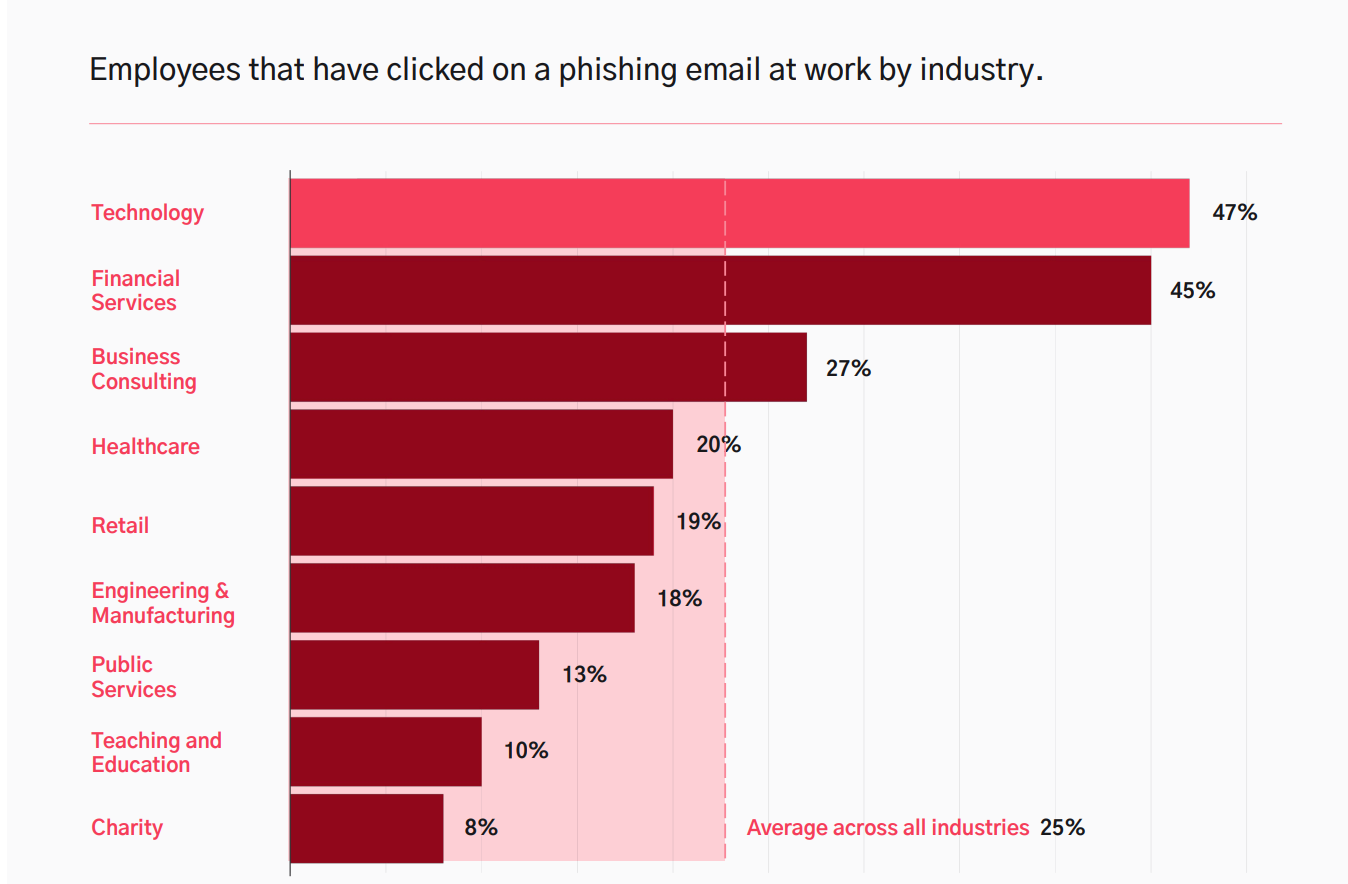
In fact, cybercriminals use social engineering in 98% of attacks. According to Kaspersky, social engineering attacks cause year-by-year over a third of all IT infrastructure incidents in businesses. What’s more, 9 of 10 businesses that have had data stolen from public cloud infrastructures say that the theft was caused by some kind of social engineering. The top three targets of the attacks were: information that confirms customer identity, customer payment information, and user authentication credentials.
Social engineering types
In general, social engineering attacks are classified into two types.
Harvesting of personal information
The first type, 'credential' or 'personal information harvesting' focuses on collecting board databases of login/password/mobile phone combinations for existing accounts on social media platforms, followed by addresses and card numbers from e-shops and subscription-based services. Such collections are later being sold on the dark web to other hackers who might use them to take over an employee's online identity (clear his account), and access all resources connected to the email/password/phone combination.
1. Phishing
Phishing uses shotgun methods to send mass emails to random people. They are disguised as notifications from government agencies, banks, charities, service providers (e-shops, websites, etc), or subscribed services. The attached malware (hidden under a link or downloadable file) will be installed on the victim’s device and collect data from every service provider they log into while using it. During COVID-19, there has been a big rise in phishing emails that look like they came from the WHO, CDC, and other government bodies.
2. Spear phishing
In this type of phishing, hackers impose formal messages sent by some sort of authority, including senior management, legal counsel, security departments, important clients, or law enforcement. It usually includes a notification/important update regarding recent events related to the victim’s interests, such as scanned documentation, money transfer, security-related patch, link to the latest newsletter, package tracking number, updated company policy, etc. Sometimes, the attack disguises a message from a customer with a downloadable link or a message from a colleague. It could also ask for proof of information and warn the victim of problems if it isn't.
The purpose of spear phishing is to trick the victim into disclosing personal information or performing actions that compromise networks, cause data loss, or cause financial loss. The email usually contains information specific to the target, such as their name and position within the company. Spear phishing targeted at high-ranked executives (i.e., C-level) is called "whaling".
3. Business email compromise (BEC)
A Business email compromise (BEC) is a type of cyberattack in which a business email address is hacked, spoofed, or impersonated. A BEC attack begins with the victim receiving an email that appears to come from a reputable business. The email appears to be genuine. However, it often has a phishing link, a malicious attachment, or a request for money to be sent to the attacker.
4. Vishing
Vishing is a type of phishing that occurs over the phone. The hacker might disguise himself as a customer service worker, concerned about the suspicious activity related to the victim’s account. They could call the target directly or leave their contact number on a fake error page that is displayed after clicking the phishing link. By putting the victim under stress (caused by potential vulnerability), the threat actor can persuade them to reveal login credentials, verification codes, security questions, or other sensitive information.
5. Smishing
In this type of phishing, fraudsters send text messages to users to trick them into downloading malware onto their phones. The main goal here is to get around two-factor authentication (2FA), which sends random access codes to a device that has been verified or infects the victim’s device to harvest passwords to different services or networks.
Social engineering in real-time
In this type of attack, the victim is forced to conduct fraudulent activities in real-time.
1. Scareware
Scareware is a type of malware commonly used in cyberattacks based on bogus errors or security breach pages. It manifests itself in the form of a popup message in a browser, claiming: "We've detected viruses on your computer! For assistance, click here.” To save the system, it is usually advised to contact the official support at the provided phone number and let the technical support remove the malware.
A victim is also instructed to not click anything – otherwise, malware will access all the computer files and delete them. This simple threat is especially effective since according to Backblaze, a shocking 38% of responders back up their devices only once a year, whereas another 20% of those who own a computer have never backed up all the data on their systems.
In essence, the hacker will employ any fear-based technique possible to convince you to click on a link. As soon as the suggested remote access tool is installed, the hacker will perform an attack with the use of RAT (remote access tools). He usually hides his actions under an "updating/restoring" black screen and proceeds to steal the data/install malware.
2. Building hacking / Unauthorised entry
Social engineering is a type of attack that is primarily based on the targets' daily habits. It’s worth noting, that attempt to gain access to a company can be treated metaphorically (as in, attack on its network) or literally – by breaking into the company's premises and manipulating its employees to grant access to the infrastructure.
The main line of defense against such attacks is usually the security of the building or its reception area. A potential hacker, for example, may appear at the reception desk pretending to be a candidate for a position in a given company, asking for a favor to print a CV from a USB flash drive, which, once attached to the computer, will install malware on it. Another common method of attack is tailgating, which involves convincing the victim with the attitude to let the facility into the premises without verification – for example, by impersonating a courier with a large, heavy package or even food delivery to a specific floor.
Some people will impersonate employees' relatives, people who need to use the restroom right away, and even facility employees. The primary goal of arriving at the reception desk is sometimes to intentionally cause confusion, allowing a hacker to bypass the checkpoint. And, as statistics show, once a person has passed the reception threshold, he or she is free to move around the company's premises.
Main stages of social engineering attack
Although there are many ways for hackers to get at a company's important data, the majority of social engineering attacks follow a similar pattern:
- Reconnaissance. By using publicly accessible materials such as company bios and structure, business-related platforms, newsfeeds, and social media, hackers gather information to identify high-level access employees. They come up with a new persona based on data leaks and out-of-office messages from a chosen company.
- Engagement. A hacker makes contact with the victim, either by approaching them in person or by reaching out via email. They maintain a professional tone and focus on building trust and dependency.
- Attack. The attack is carried out using phishing attacks, spear-phishing, voice-over IP, fraudulent websites, and a variety of other methods.
Following a successful attack, escape entails cutting off all communications and covering tracks.
Social engineering: how to defend your company data
A lot of social engineering attacks, like phishing, can be prevented by teaching your employees about the basics of cybersecurity:
- Create internal security protocols, policies, and procedures for handling sensitive information (inside and outside the company) and define the organization's communication protocol. Review them at least once every 6 months.
- Make sure that each employee knows the security procedures related to their current position. These rules say there should be a way to make sure senior management's instructions to move money or share data over the phone are real.
- Most phishing attempts can be avoided with a simple change in behavior, such as ensuring that attachments received with emails are expected and are from a legitimate source. A strong email filtering and malware scanning tool can also help stop some of these attacks.
- Review and assess the vulnerability of all types of data your business has access to and its vulnerability to social engineering and security system breakdowns. Add an extra layer of protection to the most valuable data (i.e., biometrics).
- Remember regular data backups and password change policies.
- Create a strong framework of trust at an employee level by training personnel on how to handle sensitive information and which information should not be shared outside the company (as LinkedIn phishing messages make up 47% of social media phishing attempts).
- Provide regular bite-sized reminders about typical phishing activities and desired reactions in order to prevent malicious code from being executed (and what to do if, despite that, it still will be triggered).
- Conduct regular penetration tests / red team engagements to establish your employees' vulnerabilities to social hacking with a strong emphasis on higher-level management. Spread awareness of the consequences of using phishing links.
Social engineering & cyber security – summary
Cybercriminals have become more sophisticated in their bait design and delivery, utilizing extensive dark web resources to create tailor-made spear phishing lures for their potential victims. Spear phishing social engineering scams can be as simple as a bogus email from a store asking you to change your online account password or as complex as convincingly impersonating an executive's identity. It's also a tried and true method of duping victims into downloading ransomware.
It's quick, easy, and profitable – so easy that 96% of phishing attacks arrive by email, whereas another 3% are carried out through malicious websites, and just 1% via phone. As predicted, social engineering scams will only grow in popularity as the pool of information available to bad actors on the dark web expands. As the data for February 2022 shows, another 5,1 million records were breached in 83 attacks.
Employee vulnerability can never be eliminated from businesses, but effectively educating team members about social engineering can reduce the risks, ultimately protecting your business data. Social engineering testing, training, and simulation exercises are all important in reducing the likelihood of a breach occurring. You can take positive steps toward improving resilience and risk management by reducing the likelihood of human error in particular.
Prepare your business for the risk social hacking poses to you and your company. Reach out to us @contact form and discuss your company vulnerabilities with cybersecurity experts.