Despite the fact that the cloud has simplified access to computing platforms, software, and services for many businesses, it has also introduced new cybersecurity challenges. To overcome them, you should focus on robust cloud security.
In fact, any company that decides to move data or processes to the cloud should prioritize cloud computing security. But what exactly does "cloud computing" mean? And what can we do to make it more secure?
Table of contents:
What is cloud computing?
Simply put, cloud computing uses remotely hosted computer resources as an on-demand Internet service. These resources, delivered by cloud service providers (in short: CSPs), include data storage, servers, databases, networking, and software. Cloud-based applications provide real-time data, giving you a constant view of your business's performance. A secure, reliable network connection is all that is required.
Businesses, non-profits, and other organizations all use cloud computing services on a regular basis because of their simplicity – which was especially useful during the recent lockdown. In fact, cloud computing can save storage space (by offloading physical server maintenance to a cloud provider), money (by avoiding data loss due to device failure), and time (remote access).
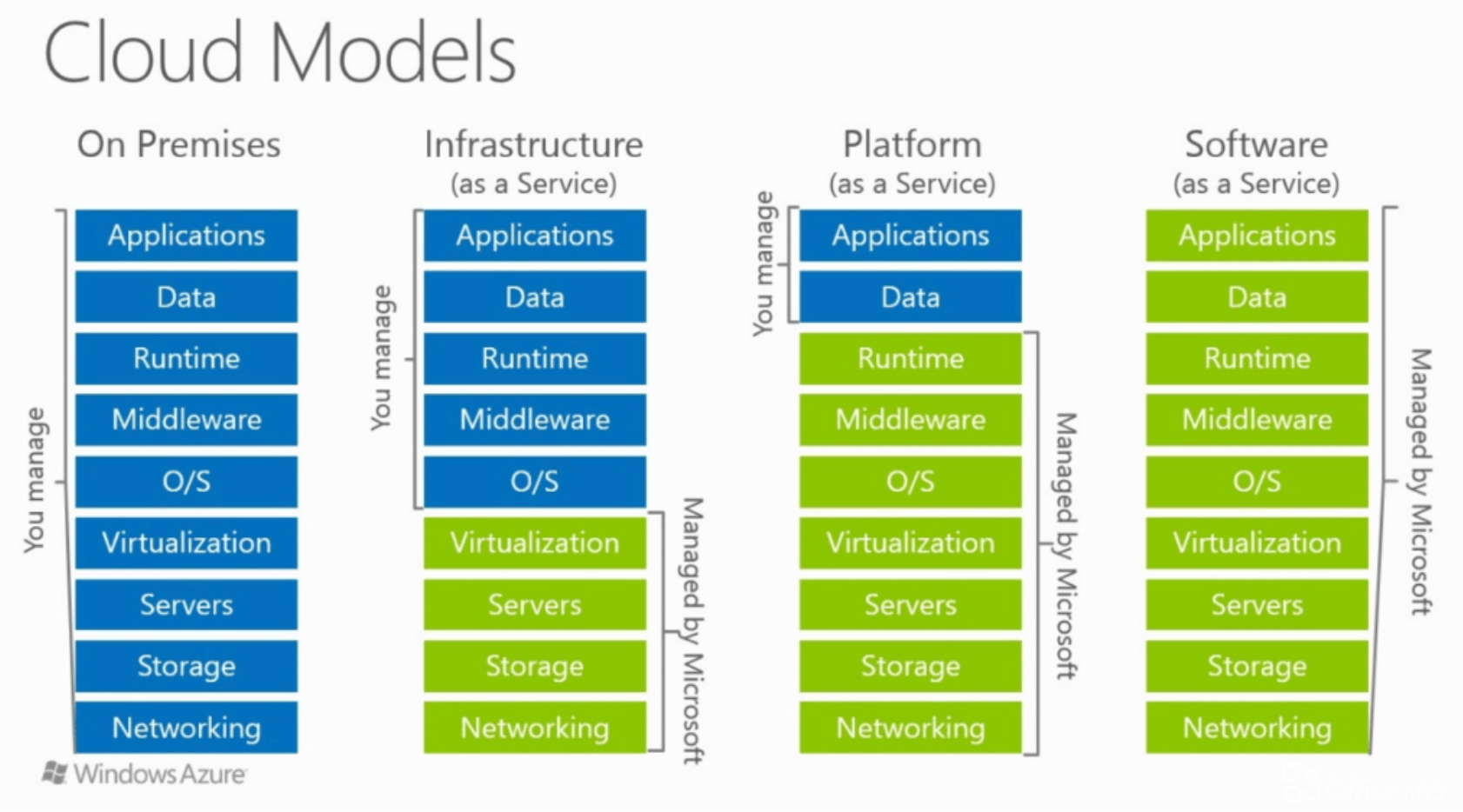
Depending on the needs of the business, various cloud models exist. Cloud services are broadly classified as:
- Software-as-a-service (SaaS) refers to software applications that are typically delivered through a web browser and hosted by external cloud infrastructure.
- Platform-as-a-service (PaaS) enables a company to use cloud resources for creating, running, and managing Web services and applications.
- Infrastructure-as-a-service (IaaS) automates the creation of virtual machines in a hosted, virtualized data center. Your company has on-demand access to computing resources with pre-configured cloud networks, operating systems, and storage.
Any of these services can help businesses access computing assets and applications without investing heavily in hardware and maintenance. Each offers different service, control, and responsibility.
In fact, the lower we are on the above scale, the more freedom we have (see the comparsion below - starting from right to the left). Which translates to a stronger need for more experienced teams on-site to ensure the systems work properly, especially when it comes to data security.
Why should businesses use cloud computing?
At this point, you should be aware that one of the best things about cloud computing is that it removes both software and hardware limits while keeping a close eye on the server's availability, capabilities, and amount of network storage.
So, no more data loss due to booted computers or unreadable pen drives. No downtime because of missing system updates, low memory on personal devices, or license problems (i.e., too many users at once). There is no longer any need to keep (and maintain) the server room. And certainly no more invoices for services purchased but never used.
Everything you require is easily accessible online via your chosen CSP platform. The technology used is always cutting-edge. The computing power is adjustable. And if you need to make some changes for whatever reason, you can regulate the cloud service settings to suit your requirements. That is, no more excessive spending.
The technology appears to be very promising, and as a result, its users will be more productive, flexible, and profitable. But if you need more convincing reasons to use cloud-based solutions in your organization, we've compiled a list of the top cloud computing benefits below.
Effortless maintenance
Forget old, incompatible systems with ineffective components. Cloud computing resources are regularly updated to maximize service potential. This feature is usually automatic, allowing the latest devices and technologies to connect easily. All of this is paired with a user-friendly design, followed by a collection of market-proven tools and solutions.
Strong resilience
The more foolproof a solution is, the more it can reduce human labor, hence the trend towards automation. In cloud computing, resilience means a service/network/data server can stay connected without losing functionality. In other words, it's the cloud network's ability to restore all functions and data after a crisis. Resilience is improved by continuous testing, often backups, and service replication. Another key elements are the processes of data backup and restoration, which should be quick and inexpensive.
Scalability
As competition grows, the business must scale. Thanks to resource pooling and multi-tenancy, CSPs are able to distribute resources among a number of clients, offering unique sets of tailored services. Hence, when a business opportunity arises, the system's capacity can be scaled up without restarting, reinstalling, or relocating the service. Due to this cloud feature, temporary workloads that require a large number of servers can be run cost-effectively as customers share the same computing resources. Despite that, each cloud customer's data is kept separate and secure.
Remote working
To access cloud data, all you need is a personal device – be it a PC, laptop, smartphone, or soon, a pair of MR glasses – and an internet connection. Using cloud resources has no geographical restrictions, which means better insight into key company statistics on demand. Furthermore, it ensures quick connections. This is especially important in post-pandemic times, when many people work remotely due to health reasons, disabilities, pregnancy, or personal preferences. Cloud computing enables remote working by providing employees with "space" to complete their tasks while staying in touch with teammates in real time.
Reporting and security
Reporting allows both the client and the service provider to keep track of which services were used and why. It's also useful for ensuring that all security precautions are in place and that the backup frequency is maintained so that everything can be restored on time. This increases efficiency and billing control.
In order to provide high-quality services to their clients, cloud service providers invest heavily in security. So, why should you, you may wonder? And what dangers should your company be guarded against?
How to protect your cloud infrastructure?
Cloud computing services provide businesses with the highest level of dependability because their users can easily and securely access their apps, projects, and data from anywhere, at any time, and on any device. The data they access is always secure due to effective cloud security solutions.
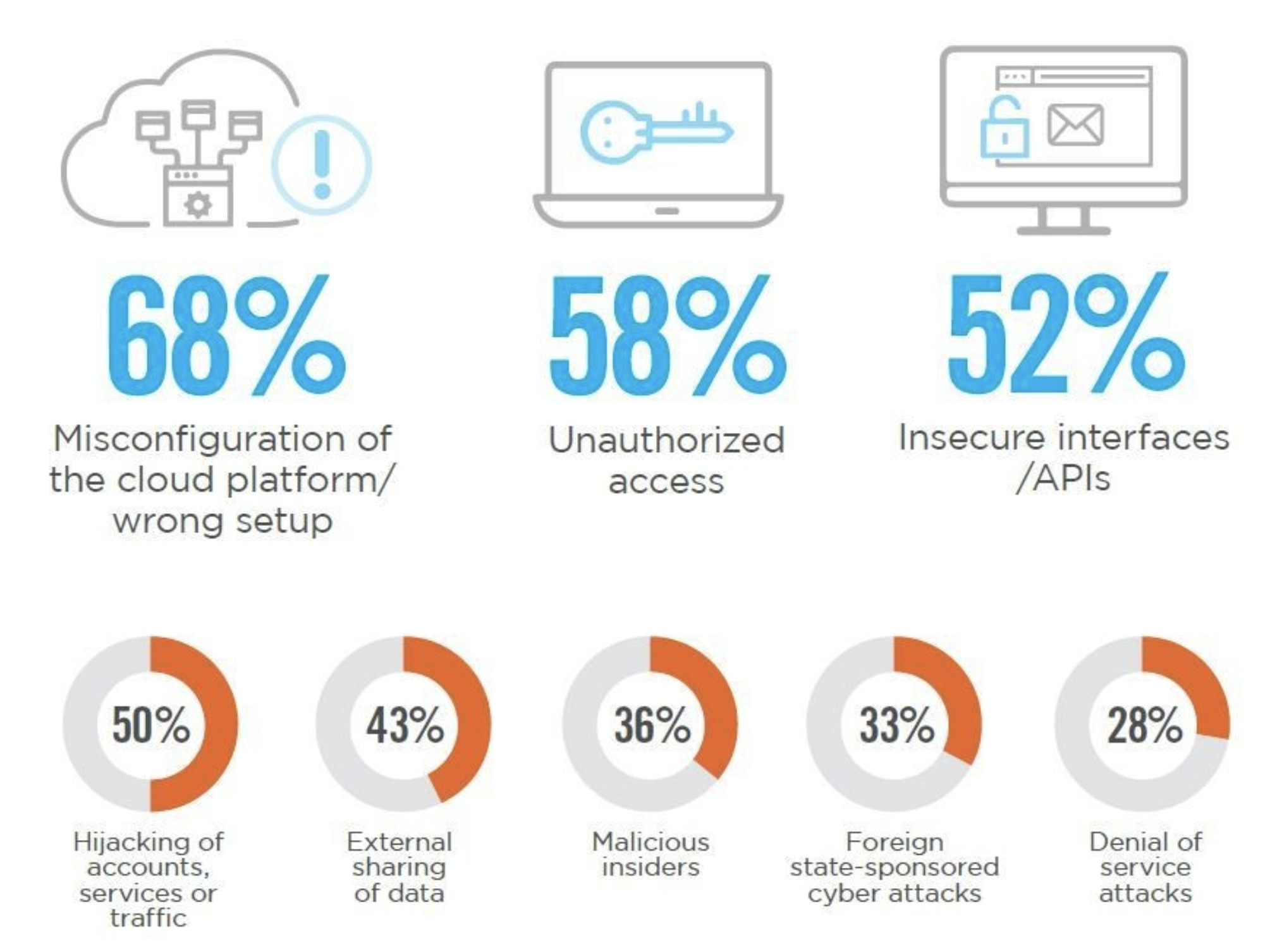
Let's quickly go over the main threats that may affect CSP clients (and their networks).
What are the dangers of using the cloud?
- Malware infection. The cloud not only allows for scalability and speed in data handling, but it also enables the rapid delivery of highly scalable malware. Malicious actors infect clouds with viruses to steal accounts and other data.
- Network compromise. Flexibility and lower costs in a shared cloud environment raise issues with data privacy and segmentation. Malicious attackers will very certainly execute brute force assaults, Trojans, SQL injection, botnets, phishing, and DDoS attacks. And because they cannot produce or block attacks, service providers are unable to identify attacks initiated on their networks.
- Data theft. Data security is the biggest challenge in cloud computing because clients rely on service providers. Improper cloud data management can cause data breaches, loss, integrity breaches, and unauthorized access.
- Account hijacking. Remote cloud computing simplifies phishing and social engineering attacks. Hackers can monitor and manipulate data by stealing weak account credentials. Phishing, spoofing, or hackers guessing a weak password can compromise password-keys.
Should I move to the cloud?
Although the majority of businesses are considering incorporating cloud computing into their operations, the security risks of doing so are successfully scaring them away. Should they be concerned in 2022? It depends.
Obviously, your cloud service provider, like any other data storage facility, can be hacked. In fact, cloud security is very similar to on-premise data center security. In both cases, the primary concern is preventing data theft, leakage, or deletion. Furthermore, due to its very nature, the cloud is extremely vulnerable to security issues, necessitating additional security precautions.
However, because granting access to the data center's infrastructure and applications is their core business model, cloud service providers can invest more resources in securing their resources than other firms. As technological advancements force CSPs to respond to emerging threats and trends, cloud security measures are constantly updated to protect clients from cybercrime. If you're concerned about database compromise, keep in mind that your data can be stolen in any case, regardless of where you store it (especially, if it could be accessed online). But, does your preferred location offer automatic backup and restoration at all times?
In fact, the risk of a data breach rises in direct proportion to the level of client autonomy within the service. In other words, the greater your desire for autonomy, the more important cloud security should be for you.
Cloud security, according to Gartner, refers to “the processes, mechanisms, and services used to control the security, compliance, and other usage risks of cloud computing”. It consists of preventive measures that reduce security vulnerabilities (for example, firewalls); automated monitoring controls that detect attacks; and corrective controls that repair the attack results (i.e., backups).
This is crucial when you consider that, while Cloud Service Providers care about the security of their infrastructure, they can't do much about your employees' dangerous habits, which may or may not include device and password sharing, using corporate email as a private one, or accessing the secured network through a public hotspot.
By implementing (and regularly reviewing) a well-designed cloud security strategy with a section dedicated to cloud infrastructure usage, you can ensure that your employees successfully contribute to boosting organizational growth while ensuring a safe and secure environment for data and apps.
So, what should this section contain?
Cloud computing security: best practices
Verify the CSP
Because no cloud architecture is completely secure, mission-critical systems and infrastructure should be moved with caution. As a result, most large and small businesses rely on well-known companies such as AWS, Microsoft Azure, and Google Cloud.
Before transferring your data to the cloud, ensure that you understand the cloud services provider's policies regarding how your data will be backed up, who will have access to different types of data, and how alleged breaches can be prevented and punished. When a security flaw is discovered, how quickly will they fix it? Are they up to date on cybersecurity and industry compliance? Does your preferred cloud computing model include built-in cloud computing security?
Control access management
Your cloud platform may have the necessary features, but in order to protect data, you and your company must implement access restrictions. To prevent data misuse, access control settings should correspond to employee responsibilities. Nobody should be able to access any additional portion of your cloud data without your permission. In fact, the fewer privileges granted to a single user, the better. Avoid super-admin functions, which are particularly appealing to hackers. It's also a good idea to use a tried-and-true combination of a strong alphanumeric password, 2FA, and a biometric (for prior accounts) to secure both high-level admin accounts and regular user profiles .
Separate and encrypt data
Create data classification policies to help separate data based on its sensitivity, as 21% of cloud-based files contained sensitive data, according to McAfee's Cloud Adoption and Risk Report. Classify data and clearly communicate within your company what data should be referred to and handled as public (accessible to all employees), private (shared with selected departments or groups), and sensitive (required to be kept private by law, contract, or policy).
Encrypt all company data to secure your cloud infrastructure. However, use your own encryption key before uploading data to the cloud to add another layer of security. Encrypted cloud data will protect you from cyberattacks and, as a result, reduce data breaches. Also, keep in mind that data management for your clients should be your top priority. Organizations must implement comprehensive data deletion rules to securely remove data while maintaining compliance. In other words, after a contract-specified data retention period, a client's data should be programmatically erased.
Educate employees
Provide frequent employee training to avoid misuse, whether caused by a lack of information or neglect. Internal security threats can be mitigated by training employees on best cloud security practices. Configure a strong password management policy within the cloud service to aid in the establishment of good habits (i.e: set auto-resetting frequency, minimal length, changes tracking).
Conduct vulnerability testing
Enterprises should conduct ongoing vulnerability testing to identify risks to ensure the latest industry-leading vulnerability and incident response tools are properly implemented. This can be accomplished by enabling automated security evaluations to learn how your cloud infrastructure is being used, revealing flaws and system gaps, and assisting in the development of better solutions.
The right cloud security strategy allows businesses to use automated cloud computing security systems with proactive features and 24/7 protection, reducing the need for human intervention. While in legacy systems, IT teams had to put out security-related "fires" after they occurred.
Take note of publicly disclosed IT failures
Read industry news for IT failures in cloud environments to stay informed as cloud use evolves and becomes more complex. High-profile failures provide critical information that can be used to ensure that your organization's cloud security risk strategy is prepared for current and future security threats.
Cloud Computing Security - Conclusion
Every day, more people use cloud computing. Large computational power and expansive data storage systems are required for ongoing corporate growth and development. And as more businesses and individuals move their IT infrastructures and data to the cloud, it's natural to have concerns about its security.
In fact, any business that conducts at least some of its workflow in the cloud should invest in cloud computing security. This is especially important in times of increased data security awareness in society, when people are becoming more conscious of collecting, storing, and exchanging their credentials. As a result, there is a strong desire for assurance that the data is managed responsibly, with data breach prevention/cybercrime protection in mind.
This tendency has already been formulated by the data protection law, which requires organizations that handle any customer data to protect it at all costs, with a special emphasis on industries that collect sensitive data related to personal health, finance, and ID.
Nonetheless, cloud computing is the future and a valuable resource for high-tech businesses that are innovative and competitive. And, if you're thinking about moving resources to the cloud, we invite you to a dedicated workshop session that will give you a thorough understanding of your organization's potential for implementing cloud computing-enabled services.